Your message has been sent.
We’ll process your request and contact you back as soon as possible.
The form has been successfully submitted.
Please find further information in your mailbox.



Now more than ever, healthcare businesses are adopting tech, and so the number of apps under attack has spiked proportionally. According to the HIPAA (Health Insurance Portability and Accountability Act) Journal, over the past 14 years, the number of reported healthcare breaches has been rising and remains sky-high today. Just last year, we saw more than 276 million breached records, including the largest ever healthcare data breach.
Here’s the thing though, after poring over the Office for Civil Rights list of reported breaches, I noticed that the majority of the cases are linked to hacking/IT incidents, theft, or unauthorized access/disclosure. After working on healthcare IT projects for years, I’ll wager you this: many of the breaches could’ve been avoided if more attention had been paid to details, like timely system updates or strengthening authentication.
In this article, I’ll walk you through the core breach risks to be aware of and the proven strategies my team and I use to keep healthcare providers’ data out of the wrong hands.
I know it, you know it: data breaches in healthcare are expensive, destructive, and, often, preventable. Financially, they can sink even well-established providers and vendors.
Let’s run the numbers. In 2025, the penalties for HIPAA Security Rule violations range from $141 to $2,134,831 per violation, depending on the medical data breach severity level. While the minimum sounds okay, the maximum penalty is about 10 times the average physician’s salary in the US.
Plus, you should remember that the authorities multiply the fines, depending on the number of violations. And these penalties don’t just affect healthcare providers: health plans, clearinghouses, and business associates of HIPAA-covered entities may face the consequences. No organization has such money to spend without flinching because of some IT failure.
On top of that, the HIPAA Breach Notification Rule requires every patient data breach that affects protected health information (PHI) to be reported, no matter the size. That means you’re not just facing consequences internally, you’re legally required to go public. And yes, such public exposure can snowball into lawsuits, investigations, and, in some cases, years of brand damage.
Plus, you’re not only breaking the bank, you’re breaking the trust — and, dare I say, in healthcare, it’s essential. A single breach may trigger an outflow of patients and damage decades-long relationships you worked on.
So, here’s the hard truth: by the end of the day, it’s far easier and cheaper to avoid HIPAA violations and severe data breaches rather than to recover from them. That’s why I always recommend proactive data protection for healthcare software development projects: you get to spot the slightest issues before the attackers do. This is one of the many ways for healthcare providers to withstand the lingering security threats.
Healthcare cyber security breaches hit record highs in the US, making the problem more and more alarming each year. In total, 734 large health data breaches were reported in 2024, and 14 of them each affected more than a million patient records. The largest incident in recent history occurred just last year, exposing the health data of over 190 million individuals in a single hacking attack. To put it into perspective: that’s more than half of the US population.
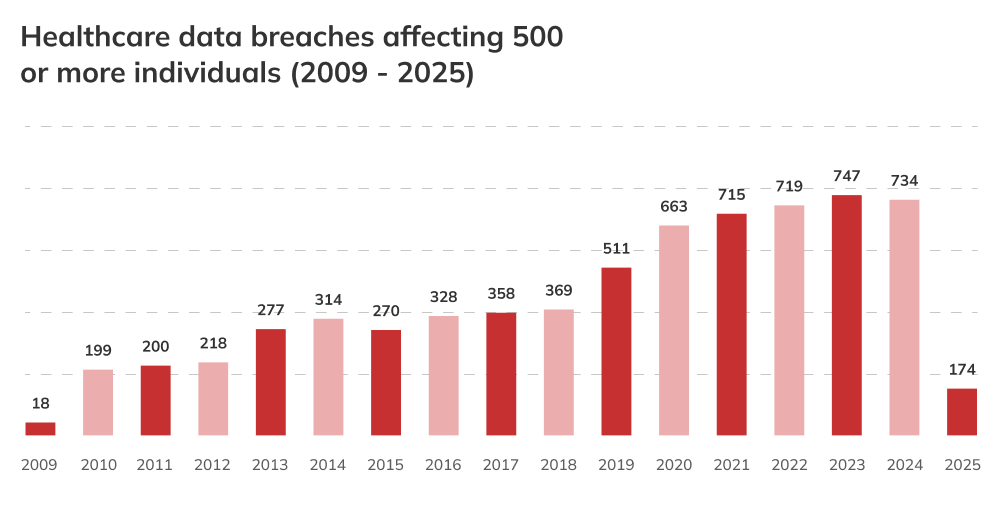
And the 2025 HIPAA breach reports’ data doesn’t promise any glimpse of hope whatsoever. As of May 2025, there have already been 174 cases reported, the majority of which involved medical providers. The way I see it, every health care breach chips away at public trust and inevitably disrupts care. So, healthcare providers should be asking themselves whether they are doing enough to prevent that from happening.
Just as I said at the beginning of this article, the root causes of most healthcare security breaches tend to fall into the same few categories. And in my experience, when auditing existing apps of the new clients, these issues are surprisingly persistent. Let’s break down the main culprits of health data breaches I see time and time again.
Despite dealing with incredibly sensitive information, many healthcare organizations still operate with data that isn’t fully (or properly) encrypted. What makes this even more concerning is that patient records often are spread across multiple systems, like EHRs, patient apps, and cloud platforms — the list goes on. Oftentimes, the security level is uneven between these systems: they were implemented at a different time, in a different environment, by different teams.
It means that not only does such an organization miss out on the benefits of healthcare data integration, but it is also compelled to maintain consistent security safeguards across all these systems (e.g., audit security of the existing systems, new connections, and subsystems). But remember, one weak point is all it takes for a data storage breach to occur. It’s harder to monitor such a fragmented landscape, and that makes exposure more likely.
Not all data breaches come from sophisticated attacks, many start with someone inside the organization. An admin sending files to the wrong recipient, a nurse forgetting to lock the PC screen before taking lunch, or a doctor clicking a phishing link without realizing it — and the data is already in danger.
Whether accidental or deliberate, internal mishandling of data remains a common cause of health data breaches. Healthcare providers tend to overlook these risks, taking more time to prepare for cyberattacks. And human factor risks remain invisible until it’s too late.
While reviewing healthcare IT solutions’ security audits, it’s shocking how inconsistent access control measures are and how broad access privileges are. Even now, not all healthcare businesses use multi-level authentication and strong password rules. Too often, users are given more access than they need to perform their daily tasks, and sometimes this access is granted indefinitely.
When user authentication mechanisms are weak or outdated, it becomes far easier for hackers to exploit those gaps and get access to everything they need. The absence of fine-grained control over who can see what makes unauthorized access one of the easiest ways for healthcare cybersecurity breaches to happen.
Healthcare providers are a prime target for ransomware attacks for one simple reason: they can’t afford to be offline for long. Doctors need access to the medical histories of dozens of patients a day to make complex, sometimes life-or-death decisions. Cybercriminals know this, and they exploit it without mercy.
The healthcare industry knows it quite well: entire hospital networks can be brought down by a single malicious attachment or an infected file. What turns these attacks into a twofold disaster is not just being locked out because of EHR security breaches, it’s the threat of stolen data being leaked.
Outdated apps are everywhere in healthcare, often because modernizing medical software feels risky or complex. Even though the bug-ridden apps seriously slow down both patient care and daily hospital workflows.
But that update delay creates a perfect window for attackers. Less diligent developers may leave vulnerabilities unpatched for months or years since they’ve come across them. Yet, something as small as a forgotten module or an unmonitored third-party tool can become the entry point for a major breach.
“Most of the time, the real problem isn’t that healthcare organizations don’t care about patient data security; it’s that they don’t have a clear picture of where the weak spots are. That’s why we always start healthcare software data protection projects with a proper audit and security testing. Once we know where the gaps are, we put together a realistic, step-by-step plan to fix them and keep patient data safe.”

Portfolio Manager in Healthcare and Medical Technologies
Now that we’ve looked at the most common issues, let’s talk about what actually works to prevent security breaches in healthcare. These aren’t just theoretical best practices, they’re things I’ve seen working successfully for multi-hospital systems and fast-growing HealthTech vendors.
Don’t make one of the biggest mistakes I see: don’t treat data security in healthcare like a single switch you flip. It’s not that easy. You need multiple defenses layered across systems, devices, users, and the physical environment. Think firewalls, endpoint detection and response (EDR), intrusion prevention systems, and encrypted communication protocols — they all should work in sync.
Every role should have access to what they need, and nothing more. We often map out access profiles early in development and validate them with stakeholders to narrow down the attack surface. Another thing here is to keep user authentication methods secure as well. Traditional passwords get stolen or reused constantly, so leaning into passwordless authentication, like biometric logins, may be a good way to reduce credential-related vulnerabilities.
Audits aren’t the most glamorous part of cybersecurity, but they’re the part that tells the truth. We run regular vulnerability scans not to tick a compliance box, but because they catch things no one may have noticed otherwise, like an outdated library or a misconfigured port. It’s always better to find these things yourself than to learn about them from a hospital security breach report.
No matter how strong the tech is, one distracted click can bring everything down. Security training isn’t about turning doctors and admin staff into tech gurus, it’s about helping them spot red flags before it’s too late. What’s worked well for our clients is short, focused sessions tied to scenarios that doctors and nurses experience every day.
Being overconfident is not the best policy when it comes to security, so you need to have an incident response plan in case anything goes wrong. At a minimum, it should define incident detection and reporting protocols, escalation chains, containment steps, communication flows (internal and external), and recovery plans. And, as cyber threats evolve constantly, we at Innowise include routine response plan reviews and refine the procedures.
Third-party vendors can be your weakest link, and it’s easy to overlook that. That’s why I always recommend checking vendors’ certifications (e.g., ISO 27001) to make sure the company can follow the required protocols. Plus, your vendor risk management protocol should include due diligence before onboarding, clearly defined data handling agreements, and security monitoring.
Advanced techs like AI and ML have become incredibly helpful, especially for spotting things humans wouldn’t catch, like subtle patterns in access logs or other suspicious activity. We use them to flag anomalies early and give teams a head start on issue elimination. As for blockchain, it’s a good tool to prove authenticity, origin, and changes in sensitive medical records.
Even the best security strategy won’t hold up if it doesn’t align with privacy and compliance requirements. These frameworks set clear expectations for how sensitive information should be handled to reduce the risk of data breaches. Here are some key considerations that often come up when talking about compliance and patient privacy.
To avoid privacy issues in healthcare, data handling is regulated by acts like HIPAA in the US, GDPR in the EU, and other region-specific legal requirements. These regulations are setting up standards on access, storage, and sharing of sensitive data and outline technical and physical safeguards that are to be implemented. Having strong, practical policies like this baked into daily operations makes compliance a part of your culture and helps you stay ahead of the breaches.
Encryption shows up again and again in privacy laws for a reason. When your data is encrypted in transit and at rest, even if your other security controls fail at some point and cyberattackers break through, they likely won’t be able to make your data readable without a proper key. That’s why, during a HIPAA or a GDPR audit, strong encryption is one of the first things regulators look for when assessing whether you did your due diligence.
When protecting healthcare data, cybersecurity frameworks like ISO 27001, ISO 27017, ISO 27018, SOC 2, and OWASP principles serve as a foundation. During the healthcare tech projects, my team and I do not treat these standards as a formality, we ingrain them into processes, controls, and documentation. The standards give you a clear structure to grow from, especially as systems scale and their complexity increases.
At the end of the day, preventing data breaches in healthcare comes down to doing the basics really well — and doing them consistently. It’s about encrypting data, controlling access, training your people, and staying on top of compliance. Nothing flashy, but these things actually work. And when you put them together, they can save you from the kind of damage no healthcare organization wants to face.
If you’re looking for expert support to prevent healthcare data breaches, let’s talk. We at Innowise help healthcare organizations build secure, compliant systems that stand up to real-world threats, so you can focus on delivering care, not putting out fires.

Senior Technical Delivery Manager in Healthcare and MedTech
Aleh has a strong grasp of what makes healthcare and MedTech software truly work. He leads with both technical clarity and sector knowledge, making sure every project delivers long-term value — not just code that runs, but systems that matter.












Your message has been sent.
We’ll process your request and contact you back as soon as possible.

By signing up you agree to our Privacy Policy, including the use of cookies and transfer of your personal information.