Ditt meddelande har skickats.
Vi behandlar din begäran och återkommer till dig så snart som möjligt.
Formuläret har skickats in framgångsrikt.
Ytterligare information finns i din brevlåda.



Digital Operational Resilience Act (DORA) har sedan den trädde i kraft blivit en avgörande faktor för hur finanssektorn hanterar IKT-risker, säkerhet och tredjepartsberoenden. Även om innebörden av DORA är tydlig i teorin - ett enhetligt ramverk för att stärka den digitala motståndskraften - är det fortfarande osäkert för många institutioner hur de ska tillämpa det på olika system, leverantörer och verksamheter.
Det här är inte bara ännu en sammanfattning av DORA-föreskrifterna. Du förstår redan vad som står på spel. Den verkliga frågan är: Är era system, samarbetspartners och interna kontroller verkligen anpassade till DORA-ramverket, och hur ser er strategi ut för långsiktig och hållbar efterlevnad?
Så slå dig ner - jag ska gå igenom vad DORA verkligen förväntar sig av ditt företag, och ännu viktigare, hur du kan uppfylla dessa förväntningar utan att sakta ner.
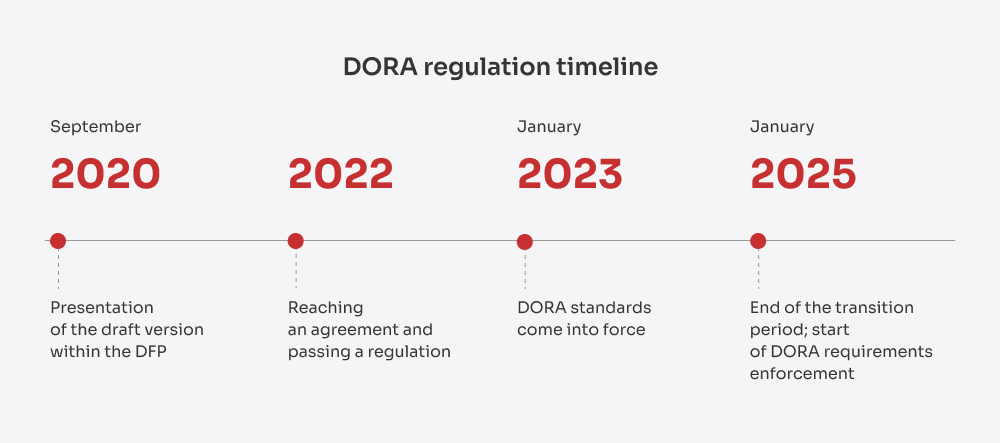
DORA, formellt känd som Förordning (EU) 2022/2554 är en bindande EU-förordning som trädde i kraft den 16 januari 2023 och började tillämpas den 17 januari 2025. Lanseringen var inte ett teoretiskt drag. Det var ett direkt svar på de eskalerande cyberhoten inom finanssektorn. I takt med att finansinstituten i allt högre grad förlitar sig på molninfrastruktur, SaaS-plattformar och andra externa partner för att leverera digitala tjänster har de också blivit mer sårbara för sammanlänkade risker som är svåra att förutse, begränsa och återhämta sig från.
Siffrorna talar sitt tydliga språk: år 2024 skulle den genomsnittliga kostnaden för ett dataintrång inom finanssektorn uppgå till $6,08 miljoner, vilket är 22% högre än det globala genomsnittet på $4,88 miljoner inom alla branscher.
Incidenter i den verkliga världen har bara förstärkt behovet av starkare motståndskraft. Under 2018 försökte TSB genomföra en stor migrering av en kärnbanksplattform. Dålig riskhantering, otillräcklig testning och ineffektiv incidenthantering ledde till omfattande avbrott som gjorde att tusentals kunder blev av med sina konton. Till följd av detta bötfällde tillsynsmyndigheterna TSB 48,65 miljoner pund för operativa risker och bristande styrning.
På samma sätt drabbades Capital One 2019 av ett massivt intrång på grund av en felkonfigurerad brandvägg i sin molninfrastruktur, vilket exponerade data från över 100 miljoner kunder. Efterspelet inkluderade $80 miljoner i straffavgifter och stora saneringskostnader.
Problemen slutade inte där. De Avbrott i CrowdStrike i juli 2024 gjorde sammankopplingen av digital infrastruktur smärtsamt uppenbar. Den utlöstes av en felaktig uppdatering och spred sig över kritiska system - flygningar fick flygförbud, bankverksamhet frystes och professionella tjänster stoppades. Det var inte bara ett tekniskt fel, det var en fullskalig kris för verksamhetens kontinuitet, vilket visar hur IKT-fel från tredje part kan få systematiska konsekvenser.
DORA blev därför EU:s svar: en heltäckande, verkställbar förordning som syftar till att överbrygga klyftan i den digitala motståndskraften genom tydlig ansvarsskyldighet, harmoniserade standarder och ett ramverk som är anpassat till dagens sammankopplade ekonomi.
Tänk så här: cybersäkerhet var tidigare något som man checkade av med årliga revisioner, några spelböcker för incidenter och en handfull isolerade policyer som gömdes undan i IT-hörnan. Men med DORA är den modellen inte längre tillräckligt bra. Nu är DORA-säkerhet allas ansvar - från ingenjörer till chefer.
Det handlar inte bara om att bevisa att man har en brandvägg - det handlar om att bevisa att hela den digitala leveranskedjan kan ta en smäll och fortsätta att fungera. DORA tar cybersäkerhet ut ur skuggorna och in i styrelserummet och tvingar företag att behandla digital risk som en affärskritisk fråga, inte bara en teknisk.

EU-förordningen DORA gäller för mer än 20 kategorier av finansiella enheter i hela EU, däribland
Men DORA:s betydelse sträcker sig bortom den traditionella finanssektorn. Förordningen innebär också att kritiska leverantörer av ICT-tjänster hamnar i strålkastarljuset när det gäller efterlevnad. Det innebär att om du levererar teknik som stöder någon av kärnfunktionerna hos en finansiell enhet - oavsett om det är molninfrastruktur, dataanalys, SaaS för betalningar eller onboarding, KYC/AML-verktyg, AI-baserad bedrägeridetektering eller till och med API-plattformar som ansluter kärnsystem - är du en del av efterlevnadskedjan nu.
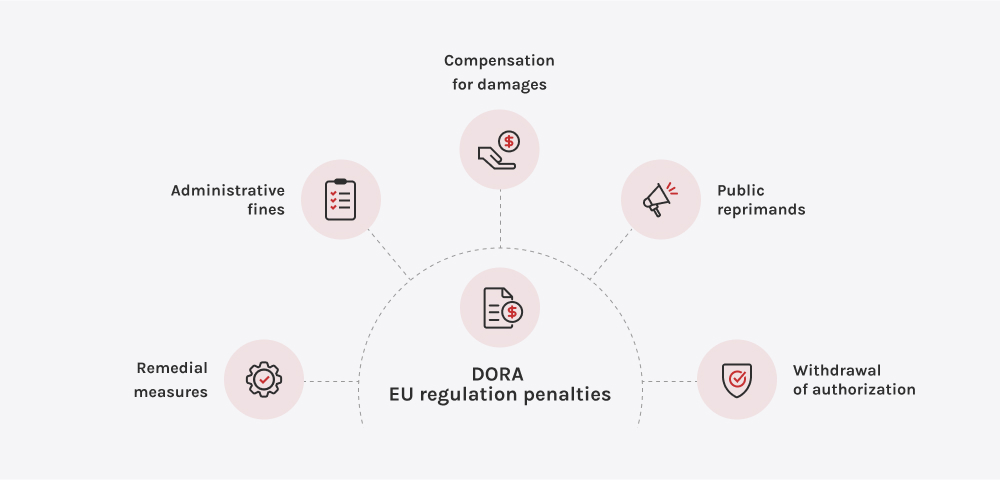
Att inte uppfylla DORA-standarderna är en risk för din verksamhet, ditt rykte och din långsiktiga strategi. Enligt DORA ska Europeiska tillsynsmyndigheter (EBA, ESMA och EIOPA) har nu befogenhet att utfärda ekonomiska sanktioner, offentliga tillrättavisningar och bindande åtgärder för avhjälpande. I fall där en tredjepartsleverantör av ICT anses utgöra ett hot mot den operativa stabiliteten ger DORA tillsynsmyndigheterna möjlighet att tvinga fram uppsägning av avtal, även med leverantörer som tillhandahåller kärninfrastruktur eller viktiga digitala tjänster.
Men de rättsliga konsekvenserna är bara en del av bilden. Den verkliga kostnaden för bristande efterlevnad är flerdimensionell:
Det är därför finansinstitut inte bara letar efter leverantörer - de letar efter resilienspartners. De vill ha teknikleverantörer som förstår DORA:s efterlevnadskrav, erbjuder granskningsbara lösningar och delar ansvar genom starka SLA:er, transparenta processer och testning i samarbete.
För finansinstituten innebär DORA-ramverket en grundläggande förändring av hur operativ motståndskraft definierar marknadsledarskap. Enbart efterlevnad är inte längre tillräckligt. DORA tvingar finansiella företag att bevisa att de kan upprätthålla kritiska tjänster genom allvarliga ICT-störningar - även när fel uppstår i outsourcade ekosystem som ligger utanför deras direkta kontroll.
Det är här det strategiska värdet uppstår:
DORA:s finansiella reglering innebär att motståndskraft omvandlas från en defensiv efterlevnadsövning till en proaktiv affärsstrategi. Institutioner som ser DORA som en möjlighet kommer att agera snabbare, återhämta sig starkare och bygga upp ett djupare förtroende än konkurrenter som fortfarande enbart fokuserar på tekniska säkerhetsåtgärder.
"På Innowise har vi noggrant analyserat DORA:s krav och stärkt vårt engagemang för digital motståndskraft på alla nivåer. Oavsett om du behöver konsulttjänster, DevSecOps-integration, tester av motståndskraft eller stöd för fullständig efterlevnad, har vi expertisen för att hålla dig i framkant. Vi har också de rätta verktygen och den operativa disciplinen för att hjälpa er att bygga framtidens säkra finanser."

Leveranschef inom FinTech
Du kanske undrar: om bestämmelser som NIS 2 (direktivet om nät- och informationssäkerhet) och GDPR (den allmänna dataskyddsförordningen) redan fanns på plats, varför behövdes då DORA? Det har du rätt i - och faktum är att NIS 2 och GDPR fortfarande spelar en viktig roll för att stärka cybersäkerheten och dataskyddet i hela EU. Den största skillnaden är dock att DORA-ramverket går längre än att skydda information. Det fokuserar på att säkerställa kontinuerlig leverans av kritiska finansiella tjänster, även under allvarliga IKT-störningar.
För att tydliggöra skillnaderna har jag sammanställt de viktigaste skillnaderna i tabellen nedan:
| Beskrivning | DORA | NIS 2 | GDPR |
| Omfattning | Gäller finansiella enheter och tredjepartsleverantörer av kritisk ICT inom hela EU:s finanssektor | Gäller för väsentliga och viktiga enheter inom kritiska sektorer i EU | Gäller globalt för organisationer som hanterar personuppgifter om EU-medborgare |
| Syfte | Stärka riskhanteringen inom ICT, tredjepartstillsynen och den operativa motståndskraften för oavbruten leverans av finansiella tjänster | Att förbättra de övergripande cybersäkerhetsstandarderna för samhällsviktiga tjänster, inklusive energi, transport, hälso- och sjukvård samt digital infrastruktur | För att skydda EU-medborgares personuppgifter och integritetsrättigheter |
| Rapportering av incidenter | Större ICT-relaterade incidenter måste rapporteras utan onödigt dröjsmål med hjälp av standardiserade mallar | Betydande cybersäkerhetsincidenter måste rapporteras inom 24 timmar till nationella myndigheter | Personuppgiftsincidenter måste rapporteras inom 72 timmar till tillsynsmyndigheten |
| Riskhantering för tredje part | Obligatorisk avtalstillsyn, övervakning och exitstrategier för tredjepartsleverantörer av kritisk ICT | Riskhantering för cybersäkerhet i leveranskedjan uppmuntras men är mindre föreskrivande jämfört med DORA | Personuppgiftsbiträden måste säkerställa säkerheten för personuppgifter, men kraven på driftsäkerhet för leverantörer är inte definierade |
| Test- och revisionskrav | Kräver periodiska tester av motståndskraft, inklusive avancerade penetrationstester med hot (TLPT) vart tredje år för kritiska enheter | Kräver riskbedömningar och allmänna åtgärder för cybersäkerhet, men inga obligatoriska standarder för motståndskraft eller penetrationstestning | Kräver lämpliga tekniska och organisatoriska säkerhetsåtgärder, men inga obligatoriska tester av motståndskraften |
| Styrning och ansvarsutkrävande | Styrelsen och ledningsorganet måste definiera, godkänna, övervaka och ansvara för hanteringen av ICT-risker | Ledningen måste godkänna cybersäkerhetsåtgärder, men styrningen av den operativa motståndskraften är mindre detaljerad | Personuppgiftsansvariga och personuppgiftsbiträden är ansvariga för dataskydd, men det finns inget specifikt krav på styrning av operativ motståndskraft |
| Enalties | Inga fastställda påföljder; nationella tillsynsmyndigheter och EU-tillsynsmyndigheter har befogenhet att utdöma böter, åtgärdsförelägganden eller kräva uppsägning av kritiska avtal med tredje part | Viktiga enheter: upp till 10 miljoner euro eller 2% av den globala omsättningen; Viktiga enheter: upp till 7 miljoner euro eller 1,4% av den globala omsättningen | Allvarliga överträdelser: upp till 20 miljoner euro eller 4% av den globala omsättningen; Mindre allvarliga överträdelser: upp till 10 miljoner euro eller 2% av den globala omsättningen |
Efterlevnaden av DORA bygger på fem pelare. Tillsammans utmanar dessa pelare finansinstituten att ompröva hur de hanterar digital risk som en central affärsförmåga. Låt oss gå igenom vad som är viktigast och hur Innowise kan hjälpa dig att ta rätt steg mot full efterlevnad.
DORA kräver att finansinstituten bygger in digital motståndskraft i alla delar av sin verksamhet - från att identifiera risker till att skydda, upptäcka, reagera och återhämta sig. Det handlar inte om att reagera efter att något har gått fel. Det handlar om att ligga steget före, minimera störningar och stärka sina system innan problemen uppstår.
Finansinstituten måste snabbt upptäcka, klassificera och rapportera IKT-relaterade incidenter till tillsynsmyndigheterna enligt strikta mallar och tidsramar. En oorganiserad eller försenad reaktion kan leda till försämrat anseende, straffavgifter eller ännu värre, att marknadens förtroende försvinner. För att uppfylla DORA:s krav måste företagen omvandla ad hoc-processer till strömlinjeformade, reviderbara arbetsflöden.
DORA kräver inte bara att företag ska hävda motståndskraft. Det krävs att de bevisar det genom regelbundna, hotledda tester av digital operativ motståndskraft (TLPT). Institutioner måste utsätta kritiska system för extrema, realistiska scenarier för att avslöja dolda sårbarheter och validera återhämtningsförmågan.
Enligt DORA är finansinstituten direkt ansvariga för motståndskraften hos sina tredjepartsleverantörer av ICT - från molntjänster och programvaruleverantörer till outsourcade IT-partner. En leverantörs misslyckande kan omedelbart bli en regulatorisk kris för dig. Det är därför som DORA:s finansreglering kräver kontinuerlig tillsyn och dokumenterade kontroller av alla ICT-partners.
DORA:s cybersäkerhetsreglering uppmuntrar finansiella enheter att aktivt dela information om cyberhot, sårbarheter och incidenter, inte som en formalitet utan som en strategisk försvarsmekanism. Genom att bidra till betrodda nätverk stärker organisationer den kollektiva motståndskraften och får information om tidiga varningar som kan förhindra större störningar.
För att uppfylla DORA:s efterlevnadskrav krävs ett tydligt och strukturerat tillvägagångssätt som kopplar samman riskhantering, incidenthantering, tredjepartstillsyn och operativa tester. Jag har kartlagt de viktigaste stegen för att hjälpa dig att gå från efterlevnad på papper till motståndskraft i praktiken.
Även om dessa steg utgör en bra utgångspunkt kommer varje företags väg till DORA-säkerhet att se lite olika ut. Du kanske behöver ett bredare spektrum, ett djupare fokus eller helt enkelt mer förtroende för att inget har missats. I dessa fall är det smartaste draget att ha experter på cybersäkerhet vid din sida - proffs som kan guida dig genom hela processen och dyka djupt in i de kritiska områdena.
För att uppnå DORA-efterlevnad krävs beprövad expertis inom cybersäkerhet, operativ motståndskraft och regleringsberedskap. På Innowise har vi en stark grund av erkända standarder, ramverk och tekniska möjligheter i den verkliga världen som är i direkt linje med DORA-krav.
Vår expertis inom regelefterlevnad och motståndskraft omfattar
Vi tillämpar bästa praxis enligt ISO 27001 för att bygga upp starka ramverk för riskhantering, styrning och incidenthantering, vilket är den kritiska grunden för efterlevnad av DORA.
Vi strukturerar våra program för motståndskraft kring NIST-principerna, som omfattar hotidentifiering, skydd, upptäckt, svar och återställning, helt i linje med DORA:s operativa riskstrategi.
När vi levererar molntjänster eller hanterade tjänster säkerställer vår SOC 2-överensstämmelse robusta kontroller av datasäkerhet, tillgänglighet och sekretess för att stödja DORA:s krav på tredjepartstillsyn.
Vi använder ledande CSPM-verktyg (som Chef Compliance, tfsec, OpenSCAP, CloudBots) för att upptäcka och åtgärda felkonfigurationer i molnmiljöer och därmed minska den operativa risken.
Verktyg som ELK, Nagios, Prometheus, Grafana och Kibana gör det möjligt för oss att leverera efterlevnadsstatus i realtid, insikter om incidenter och trender för motståndskraft, vilket är avgörande för DORA:s förväntningar på övervakning och rapportering.
Våra utvecklings- och driftsmetoder omfattar förhandsgodkända efterlevnadskontroller med hjälp av verktyg som Terraform och Ansible, vilket säkerställer att vi är redo för lagstiftning i varje steg av teknikens livscykel.
Regelbundna granskningar av motståndskraften med hjälp av plattformar som Lynis, Wazuh, Checkov, OpenSCAP och CIS-CAT håller rutinerna för operativ motståndskraft aktuella och redo för granskning av tillsynsmyndigheter.
DORA skakar om finansvärlden - och inte i det tysta. Regleringen är nu i full gång, men för många institutioner och leverantörer känns saker och ting fortfarande lite osäkra. Jag har haft otaliga samtal på senare tid med tekniska chefer, efterlevnadsteam och styrelseledamöter som försöker packa upp DORA-betydelsen i verkliga, operativa termer. Jag har därför sammanställt de vanligaste frågorna jag får - och hur jag ser att det hela kommer att utvecklas.
Nu när DORA är i drift har de flesta finansinstitut gått från planering till handling. Men så här ser verkligheten ut - många företag har fortfarande inte nått ända fram. Enligt en McKinsey-undersökning från mitten av 2024 kände sig bara omkring en tredjedel av företagen säkra på att de skulle uppfylla alla DORA-krav senast i januari 2025. Till och med de som var säkra på sin sak medgav att de skulle behöva stryka ut processer långt in på det här året. Den största smärtpunkten? Att hantera tredjepartsrisker i stor skala. För många har det varit ett projekt i sig att bara ta reda på vilka leverantörer som räknas som "kritiska" enligt DORA-ramverket.
Så vad är det egentligen som händer på fältet? Teamen blir allt mer organiserade. Företagen inrättar särskilda DORA-program, involverar personer från IT, juridik, efterlevnad och inköp och investerar i plattformar som samlar allt under ett tak. Det finns också en växande övergång från att behandla DORA som "ännu en IT-grej" till att göra det till en diskussion på styrelsenivå. En återkommande utmaning är att arbeta med mindre teknikleverantörer som helt enkelt inte har resurserna att uppfylla alla krav på efterlevnad. Det innebär att vissa finansinstitut nu agerar som supportpartners, inte bara som kunder.
Och trycket stannar inte vid DORA. Inom EU skärper NIS 2 reglerna för kritisk infrastruktur, och Cyber Resilience Act är på väg att sätta säkerhet på produktnivå under lupp. Samtidigt följer tillsynsmyndigheter utanför EU utvecklingen noga. FCA och PRA i Storbritannien har redan infört sina egna regler för motståndskraft, och i USA förväntar sig SEC nu att börsbolag ska redovisa hur de hanterar cyberrisker. Om du tänker långsiktigt är DORA:s finansregler inte bara en europeisk regel - det är en global utgångspunkt.
AI för regelefterlevnad kommer definitivt att spela en större roll - inte bara i teorin utan även i den dagliga verksamheten. Många team använder redan NLP-verktyg (Natural Language Processing) för att gå igenom stora högar med kontrakt och leverantörsavtal. Dessa verktyg hjälper till att automatiskt upptäcka varningssignaler, som avsaknad av revisionsrättigheter eller vaga garantier för återställningstid. Istället för att förlita sig på att jurister eller efterlevnadsansvariga ska gå igenom varje rad manuellt, använder företagen AI för att flagga för risker i förväg och se till att dokumentationen är strikt från dag ett.
På automatiseringssidan går saker och ting snabbt. Verktyg som SOAR - det vill säga Security Orchestration, Automation och Response - gör det mycket enklare att hantera incidenter utan kaos. Låt oss säga att något går sönder. Dessa plattformar kan utlösa varningar, låsa ner saker och ting och till och med generera den första DORA-kompatibla rapporten för tillsynsmyndigheter, allt utan att en människa först behöver ingripa. Och GRC-plattformar som ServiceNow eller MetricStream håller också på att utvecklas. De lägger till smarta instrumentpaneler, automatiserade tester av motståndskraft och robotar som påminner teamen om när de ska köra övningar eller kontrollera tredjeparts-KPI:er.
DORA reglerar inte teknikleverantörer direkt, men det håller finansinstitut fullt ansvariga för motståndskraften i den programvara de använder. Det är en stor sak. Det innebär att banker, försäkringsbolag och fintech-företag inte längre bara kan välja ett utvecklingsteam baserat på hastighet eller budget. Om din kod hamnar i något som på långt när är kritiskt - som betalningar, onboarding, handelsplattformar - måste din kund bevisa att programvaran är säker, testad och spårbar från början till slut.
Så hur ser det egentligen ut i praktiken? Upphandlingsteam ber nu om saker som säker SDLC-dokumentation, automatiserade testloggar och rapporter om sårbarhetsskanning direkt på förhand. Kontrakten uppdateras med klausuler om motståndskraft som omfattar allt från återställningstider för säkerhetskopior till ansvar för incidenthantering. Vissa företag genomför till och med gemensamma testsessioner med sina leverantörer för att stresstesta svarstiderna. Slutsatsen är att om du bygger finansiell programvara för en kund, är du en del av deras compliance-berättelse nu.
Jag hoppas att du efter det här inlägget känner dig lite mer säker på DORA - eller åtminstone ställer dig själv de rätta frågorna. Och ärligt talat, det är redan ett stort steg. Oavsett om du precis har börjat packa upp förordningen eller är i full färd med att implementera den, behöver vägen till efterlevnad inte vara överväldigande.
På Innowise finns vi här för att hjälpa dig att förstå DORA-labyrinten, bygga upp en verklig digital motståndskraft och skydda ditt företag, inte bara nu, utan även för vad som komma skall.

FinTech-expert
Siarhei leder vår FinTech-verksamhet med djup branschkunskap och en tydlig bild av vart digital finansiering är på väg. Han hjälper kunder att navigera i komplexa regelverk och tekniska val, och utformar lösningar som inte bara är säkra - utan också byggda för tillväxt.









Ditt meddelande har skickats.
Vi behandlar din begäran och återkommer till dig så snart som möjligt.

Genom att registrera dig godkänner du vår Integritetspolicy, inklusive användning av cookies och överföring av din personliga information.