Meldingen din er sendt.
Vi behandler forespørselen din og kontakter deg så snart som mulig.
Skjemaet har blitt sendt inn.
Mer informasjon finner du i postkassen din.



Siden loven om digital robusthet (Digital Operational Resilience Act, DORA) trådte i kraft, har den blitt en avgjørende faktor for hvordan finanssektoren håndterer IKT-risiko, sikkerhet og avhengigheter til tredjeparter. Selv om DORA i teorien er et klart og tydelig rammeverk for å styrke den digitale robustheten, er det fortsatt mange institusjoner som famler i blinde når de skal anvende det på tvers av systemer, leverandører og operasjoner.
Dette er ikke bare nok et sammendrag av DORA-forskriften. Du forstår allerede hva som står på spill. Det virkelige spørsmålet er: Er systemene, samarbeidspartnerne og internkontrollen din virkelig tilpasset DORA-rammeverket, og hva er strategien din for langsiktig og bærekraftig etterlevelse?
Så sett deg ned - jeg skal gå gjennom hva DORA egentlig forventer av virksomheten din, og enda viktigere, hvordan du kan innfri disse forventningene uten å bremse opp.
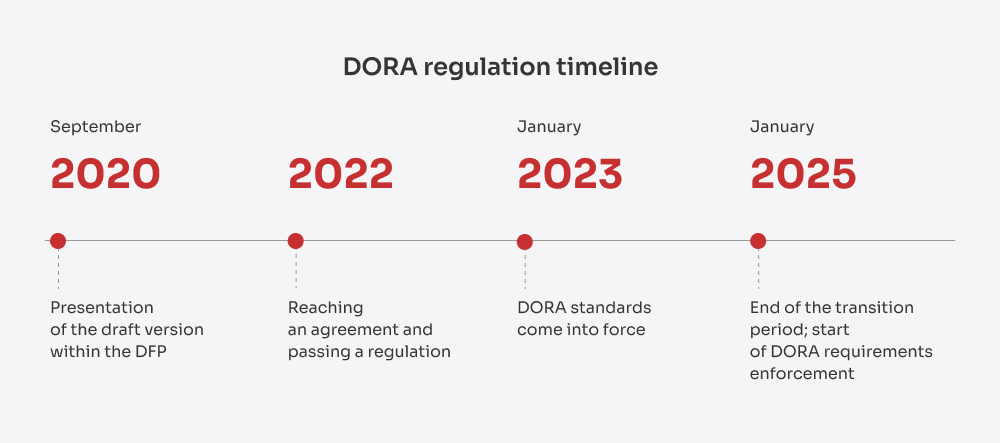
DORA, tidligere kjent som Forordning (EU) 2022/2554 er en bindende EU-forordning som trådte i kraft 16. januar 2023 og ble gjeldende fra 17. januar 2025. Lanseringen var ikke et teoretisk trekk. Den var et direkte svar på de økende cybertruslene i finanssektoren. Etter hvert som finansinstitusjonene i stadig større grad baserer seg på skyinfrastruktur, SaaS-plattformer og andre eksterne partnere for å levere digitale tjenester, har de også blitt mer sårbare for sammenkoblede risikoer som det er vanskelig å forutse, begrense og gjenopprette.
Tallene taler for seg selv: I 2024 vil den gjennomsnittlige kostnaden for et datainnbrudd i finanssektoren være $6,08 millioner, som er 22% høyere enn det globale gjennomsnittet på $4,88 millioner på tvers av alle bransjer.
Hendelser i den virkelige verden har bare forsterket behovet for sterkere motstandsdyktighet. I 2018 forsøkte TSB å migrere en stor kjernebankplattform. Dårlig risikostyring, utilstrekkelig testing og ineffektiv hendelseshåndtering førte til omfattende strømbrudd, og tusenvis av kunder ble stengt ute fra kontoene sine. Som et resultat av dette ble tilsynsmyndighetene ilagt en bot TSB 48,65 millioner pund for operasjonell risiko og styringssvikt.
I 2019 ble Capital One utsatt for et massivt sikkerhetsbrudd på grunn av en feilkonfigurert brannmur i skyinfrastrukturen, noe som eksponerte data fra over 100 millioner kunder. Ettervirkningene inkluderte $80 millioner i bøter og store utbedringskostnader.
Problemene stoppet ikke der. De CrowdStrike strømbrudd i juli 2024 gjorde sammenkoblingen av digital infrastruktur smertelig tydelig. Den ble utløst av en feilaktig oppdatering, og spredte seg til alle kritiske systemer - fly ble satt på bakken, bankvirksomhet ble frosset og profesjonelle tjenester stanset. Det var ikke bare en teknisk feil; det var en fullskala kontinuitetskrise som demonstrerte hvordan tredjeparts IKT-feil kan få systemiske konsekvenser.
DORA ble derfor EUs svar: et omfattende regelverk som kan håndheves, og som er utviklet for å tette gapet i den digitale robustheten med tydelig ansvarlighet, harmoniserte standarder og et rammeverk som passer for dagens sammenkoblede økonomi.
Tenk på det på denne måten: Tidligere var cybersikkerhet noe du sjekket av med årlige revisjoner, noen hendelseshåndbøker og en håndfull silo-policyer gjemt i IT-hjørnet. Men med DORA er ikke den modellen lenger god nok. Nå er DORA-sikkerhet alles ansvar - fra ingeniører til ledere.
Det handler ikke bare om å bevise at man har en brannmur - det handler om å bevise at hele den digitale forsyningskjeden kan tåle en smell og fortsette å fungere. DORA bringer cybersikkerhet ut av skyggen og inn i styrerommet, og tvinger selskaper til å behandle digital risiko som et forretningskritisk problem, ikke bare et teknisk problem.

DORA EU-forordningen gjelder for mer enn 20 kategorier av finansielle enheter i hele EU, blant annet
Men DORA har ikke bare betydning for den tradisjonelle finanssektoren. Forordningen setter også leverandører av kritiske IKT-tjenester i søkelyset. Det betyr at hvis du leverer teknologi som støtter en av kjernefunksjonene til en finansiell enhet - enten det er skyinfrastruktur, dataanalyse, SaaS for betalinger eller onboarding, KYC/AML-verktøy, AI-basert svindeloppdagelse eller til og med API-plattformer som kobler sammen kjernesystemer - er du nå en del av compliance-kjeden.
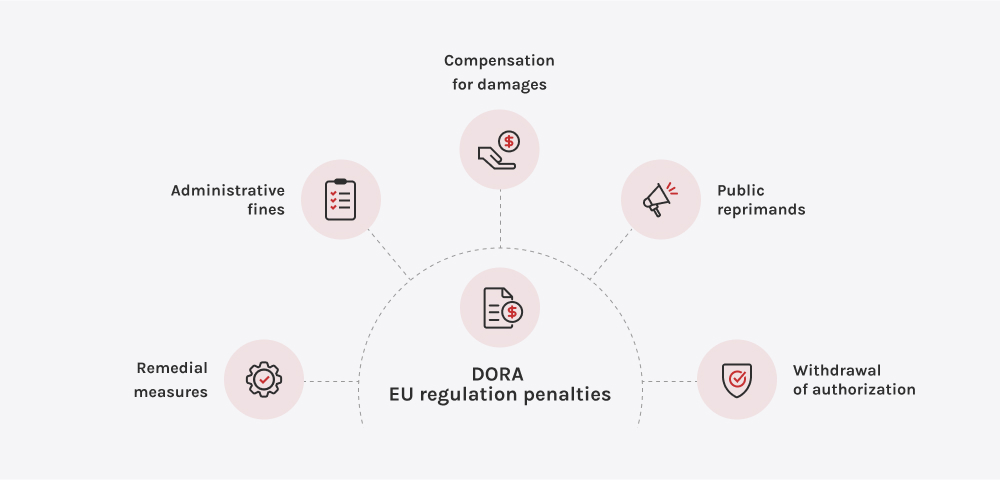
Å ikke oppfylle DORA-standardene er en risiko for virksomheten, omdømmet og den langsiktige strategien. I henhold til DORA skal Europeiske tilsynsmyndigheter (EBA, ESMA og EIOPA) har nå myndighet til å utstede økonomiske sanksjoner, offentlige irettesettelser og bindende utbedringstiltak. I tilfeller der en tredjepartsleverandør av IKT anses å utgjøre en trussel mot driftsstabiliteten, gir DORA tilsynsmyndighetene mulighet til å tvinge frem en oppsigelse av kontrakter, også med leverandører som leverer kjerneinfrastruktur eller viktige digitale tjenester.
Men konsekvensene av regelverket er bare en del av bildet. De reelle kostnadene ved manglende etterlevelse er flerdimensjonale:
Derfor er finansinstitusjonene ikke bare på utkikk etter leverandører - de er på utkikk etter robuste partnere. De vil ha teknologileverandører som forstår kravene i DORA, tilbyr løsninger som kan revideres, og som deler ansvaret gjennom sterke SLA-er, transparente prosesser og samarbeidstesting.
For finansinstitusjonene markerer DORA-rammeverket et fundamentalt skifte i hvordan operasjonell robusthet definerer markedslederskap. Etterlevelse alene er ikke lenger nok. DORA tvinger finansforetakene til å bevise at de kan opprettholde kritiske tjenester gjennom alvorlige IKT-avbrudd - selv når det oppstår feil i utkontrakterte økosystemer utenfor deres direkte kontroll.
Det er her den strategiske verdien oppstår:
DORA-regelverket forvandler resiliens fra en defensiv compliance-øvelse til en proaktiv forretningsstrategi. Institusjoner som ser på DORA som en mulighet, vil komme seg raskere, stå sterkere og bygge dypere tillit enn konkurrenter som fortsatt fokuserer utelukkende på tekniske sikkerhetstiltak.
"Vi i Innowise har analysert DORAs krav grundig og forsterket vårt engasjement for digital robusthet på alle nivåer. Enten du trenger rådgivning, DevSecOps-integrasjon, robusthetstesting eller full compliance-støtte, har vi ekspertisen som skal til for å holde deg i forkant. Vi har også de riktige verktøyene og den operasjonelle disiplinen som skal til for å hjelpe deg med å bygge fremtidens sikre finanssektor."

Leveransesjef i FinTech
Du lurer kanskje på hvorfor DORA i det hele tatt var nødvendig, når regelverk som NIS 2 (Network and Information Security Directive) og GDPR (General Data Protection Regulation) allerede var på plass? Det er et godt poeng - og faktisk spiller NIS 2 og GDPR fortsatt en viktig rolle når det gjelder å styrke cybersikkerheten og databeskyttelsen i hele EU. Den viktigste forskjellen er imidlertid at DORA-rammeverket går lenger enn å beskytte informasjon. Det fokuserer på å sikre kontinuerlig levering av kritiske finansielle tjenester, selv under alvorlige IKT-avbrudd.
For å gjøre forskjellene tydelige, har jeg samlet de viktigste forskjellene i tabellen nedenfor:
| Beskrivelse | DORA | NIS 2 | GDPR |
| Omfang | Gjelder for finansielle enheter og kritiske IKT-tredjeleverandører i hele EUs finanssektor | Gjelder for essensielle og viktige enheter i kritiske sektorer i EU | Gjelder globalt for organisasjoner som håndterer personopplysninger om EU-borgere |
| Formål | Styrke IKT-risikostyring, tredjepartsovervåking og operasjonell robusthet for uavbrutt levering av finansielle tjenester | Å forbedre de generelle standardene for cybersikkerhet i alle viktige tjenester, inkludert energi, transport, helsetjenester og digital infrastruktur | For å beskytte EU-borgernes personopplysninger og personvernrettigheter |
| Rapportering av hendelser | Større IKT-relaterte hendelser skal rapporteres uten unødig forsinkelse ved hjelp av standardiserte maler | Betydelige cybersikkerhetshendelser må rapporteres innen 24 timer til nasjonale myndigheter | Brudd på personopplysningssikkerheten må rapporteres til tilsynsmyndigheten innen 72 timer |
| Tredjeparts risikostyring | Obligatorisk kontraktsmessig tilsyn, overvåking og exit-strategier for kritiske IKT-tredjeleverandører | Risikostyring for cybersikkerhet i leverandørkjeden oppfordres, men er mindre preskriptiv enn DORA | Databehandlere må sørge for sikkerheten til personopplysninger, men det er ikke definert krav til leverandørers driftssikkerhet |
| Test- og revisjonskrav | Krever periodisk testing av motstandsdyktighet, inkludert avansert trusselstyrt penetrasjonstesting (TLPT) hvert tredje år for kritiske enheter | Krever risikovurderinger og generelle cybersikkerhetstiltak, men ingen obligatoriske standarder for motstandsdyktighet eller penetrasjonstesting | Krever egnede tekniske og organisatoriske sikkerhetstiltak, men ingen obligatorisk resiliensprøving |
| Styring og ansvarlighet | Styret og ledelsen må definere, godkjenne, føre tilsyn med og stå til ansvar for IKT-risikostyring | Ledelsen må godkjenne cybersikkerhetstiltak, men styringen av operasjonell robusthet er mindre detaljert | Behandlingsansvarlige og databehandlere er ansvarlige for personvern, men det er ikke noe spesifikt krav om styring av operasjonell robusthet |
| Enalties | Ingen faste sanksjoner definert; nasjonale og europeiske tilsynsmyndigheter har myndighet til å ilegge bøter, pålegg om utbedring eller pålegge oppsigelse av kritiske tredjepartskontrakter | Viktige enheter: opp til 10 millioner euro eller 2% av den globale omsetningen; Viktige enheter: opptil 7 millioner euro eller 1,41 T64T av den globale omsetningen | Alvorlige brudd: opptil 20 millioner euro eller 4% av den globale omsetningen; Mindre alvorlige brudd: opptil 10 millioner euro eller 2% av den globale omsetningen |
DORA bygger på fem pilarer. Til sammen utfordrer disse pilarene finansinstitusjonene til å tenke nytt om hvordan de håndterer digital risiko som en del av kjernevirksomheten. La oss gå gjennom hva som er viktigst, og hvordan Innowise kan hjelpe deg med å ta de riktige stegene mot full etterlevelse.
DORA krever at finansinstitusjonene bygger inn digital robusthet i alle deler av virksomheten - fra å identifisere risikoer til å beskytte, oppdage, reagere og gjenopprette. Det handler ikke om å reagere etter at noe går galt. Det handler om å ligge ett skritt foran, minimere avbrudd og styrke systemene før problemene oppstår.
Finansinstitusjoner må oppdage, klassifisere og rapportere IKT-relaterte hendelser til tilsynsmyndighetene raskt, i henhold til strenge maler og tidsfrister. En uorganisert eller forsinket respons kan føre til skade på omdømmet, bøter fra myndighetene eller, enda verre, tap av tillit i markedet. For å oppfylle kravene fra DORA må virksomhetene gjøre ad hoc-prosesser om til strømlinjeformede, reviderbare arbeidsflyter.
DORA krever ikke bare at virksomhetene hevder at de er robuste. De må også bevise det gjennom regelmessige, trusselstyrte tester av digital operativ robusthet (TLPT). Institusjonene må utsette kritiske systemer for ekstreme, realistiske scenarier for å avdekke skjulte sårbarheter og validere gjenopprettingsmulighetene.
I henhold til DORA er finansinstitusjonene direkte ansvarlige for robustheten til sine tredjeparts IKT-leverandører - fra skytjenester og programvareleverandører til outsourcede IT-partnere. En leverandørs svikt kan umiddelbart bli en regulatorisk krise for dere. Derfor krever DORA-regelverket kontinuerlig tilsyn og dokumenterte kontroller av alle IKT-partnere.
DORAs cybersikkerhetsforskrift oppfordrer finansforetak til aktivt å dele informasjon om cybertrusler, sårbarheter og hendelser, ikke som en formalitet, men som en strategisk forsvarsmekanisme. Ved å bidra til pålitelige nettverk styrker organisasjoner den kollektive motstandskraften og får tidlig varsling som kan forhindre større forstyrrelser.
For å oppfylle kravene i DORA kreves det en klar og strukturert tilnærming som knytter sammen risikostyring, hendelsesrespons, tredjepartstilsyn og driftstesting. Jeg har kartlagt de viktigste trinnene for å hjelpe deg med å gå fra samsvar på papiret til motstandsdyktighet i praksis.
Selv om disse trinnene gir et solid utgangspunkt, vil veien til DORA-sikkerhet se litt forskjellig ut for hver enkelt bedrift. Kanskje trenger dere et bredere omfang, et dypere fokus eller rett og slett mer tillit til at dere ikke har gått glipp av noe. I slike tilfeller er det smartest å ha cybersikkerhetseksperter ved din side - fagfolk som kan veilede deg gjennom hele prosessen og dykke dypt ned i de kritiske områdene.
For å oppnå samsvar med DORA kreves det dokumentert ekspertise innen cybersikkerhet, operasjonell robusthet og regulatorisk beredskap. Innowise har et sterkt fundament av anerkjente standarder, rammeverk og tekniske ferdigheter som er direkte i tråd med DORA-krav.
Vår ekspertise innen compliance og robusthet omfatter
Vi bruker beste praksis fra ISO 27001 for å bygge sterke rammeverk for risikostyring, styring og hendelsesrespons, som er det avgjørende grunnlaget for samsvar med DORA.
Vi strukturerer våre robusthetsprogrammer rundt NIST-prinsippene, som dekker trusselidentifisering, beskyttelse, deteksjon, respons og gjenoppretting, helt i tråd med DORAs tilnærming til operasjonell risiko.
Når vi leverer nettskytjenester eller administrerte tjenester, sørger SOC 2-samsvaret vårt for robuste kontroller av datasikkerhet, tilgjengelighet og konfidensialitet for å støtte DORAs krav til tredjepartstilsyn.
Vi bruker ledende CSPM-verktøy (som Chef Compliance, tfsec, OpenSCAP, CloudBots) til å oppdage og fikse feilkonfigurasjoner i skymiljøer, og reduserer dermed den operasjonelle risikoen.
Verktøy som ELK, Nagios, Prometheus, Grafana og Kibana gjør det mulig for oss å levere samsvarsstatus i sanntid, innsikt i hendelser og trender for robusthet, noe som er avgjørende for DORAs forventninger til overvåking og rapportering.
Våre utviklings- og driftspraksiser omfatter forhåndsgodkjente samsvarskontroller ved hjelp av verktøy som Terraform og Ansible, noe som sikrer at vi er klare til å følge regelverket i alle faser av teknologiens livssyklus.
Regelmessige robusthetsrevisjoner ved hjelp av plattformer som Lynis, Wazuh, Checkov, OpenSCAP og CIS-CAT sørger for at praksisen for driftsstabilitet er oppdatert og klar for regulatoriske kontroller.
DORA ryster finansverdenen - og det går ikke stille for seg. Reguleringen er nå i full gang, men for mange institusjoner og leverandører føles ting fortsatt litt usikre. Jeg har hatt utallige samtaler med teknologisjefer, compliance-team og styremedlemmer i det siste for å prøve å finne ut hva DORA betyr i praksis. Jeg har derfor satt opp de vanligste spørsmålene jeg får - og hvordan jeg ser for meg at det hele vil utfolde seg.
Nå som DORA er i drift, har de fleste finansinstitusjoner gått fra å planlegge til å gjennomføre. Men realiteten er at mange selskaper fortsatt ikke har kommet helt i mål. Ifølge en McKinsey-undersøkelsen fra midten av 2024, var det bare rundt en tredjedel av bedriftene som følte seg sikre på at de ville oppfylle alle DORA-kravene innen januar 2025. Selv de som var sikre, innrømmet at de ville jobbe med å forbedre prosessene langt ut i dette året. Det største smertepunktet? Håndtering av tredjepartsrisiko i stor skala. For mange har bare det å finne ut hvilke leverandører som regnes som "kritiske" i henhold til DORA-rammeverket, vært et prosjekt i seg selv.
Så hva skjer egentlig på bakken? Teamene blir mer organiserte. Bedrifter oppretter egne DORA-programmer, trekker inn folk fra IT, juridisk avdeling, compliance og innkjøp, og investerer i plattformer som samler alt under ett tak. Det er også en økende tendens til å gå fra å behandle DORA som "bare enda en IT-greie" til å gjøre det til en diskusjon på styrenivå. En tilbakevendende utfordring er å samarbeide med mindre teknologileverandører som rett og slett ikke har ressurser til å oppfylle alle kravene. Det betyr at noen finansinstitusjoner nå opptrer som støttepartnere, ikke bare som kunder.
Og presset stopper ikke ved DORA. I EU strammer NIS 2 inn reglene for kritisk infrastruktur, og Cyber Resilience Act er i ferd med å sette sikkerhet på produktnivå under lupen. Samtidig følger tilsynsmyndigheter utenfor EU nøye med. FCA og PRA i Storbritannia har allerede innført sine egne regler for robusthet, og i USA forventer SEC nå at børsnoterte selskaper offentliggjør hvordan de håndterer cyberrisiko. Hvis du tenker langsiktig, er ikke DORA-regelverket bare en europeisk regel - det er et globalt utgangspunkt.
AI for samsvar med regelverk kommer definitivt til å spille en større rolle - ikke bare i teorien, men i den daglige driften. Mange team bruker allerede NLP-verktøy (Natural Language Processing) til å gå gjennom enorme bunker med kontrakter og leverandøravtaler. Disse verktøyene bidrar til å oppdage røde flagg automatisk, for eksempel manglende revisjonsrettigheter eller vage garantier for gjenopprettingstid. I stedet for å stole på at advokater eller compliance-ansvarlige skanner gjennom hver eneste linje manuelt, tar selskapene i bruk kunstig intelligens for å avdekke risikoer på forhånd og sørge for at dokumentasjonen er tett fra dag én.
På automatiseringssiden går utviklingen raskt. Verktøy som SOAR - Security Orchestration, Automation and Response - gjør det mye enklere å håndtere hendelser uten kaos. La oss si at noe går i stykker. Disse plattformene kan utløse varsler, låse ting ned og til og med generere den første DORA-kompatible rapporten til tilsynsmyndighetene, alt uten at et menneske må gripe inn først. Og GRC-plattformer som ServiceNow eller MetricStream er også på vei opp. De legger til smarte dashbord, automatisert testing av robusthet og roboter som minner teamene på når de skal kjøre øvelser eller sjekke tredjeparts KPI-er.
DORA regulerer ikke teknologileverandørene direkte, men det holder finansinstitusjonene fullt ut ansvarlige for robustheten til programvaren de bruker. Det er en stor sak. Det betyr at banker, forsikringsselskaper og fintech-selskaper ikke lenger bare kan velge et utviklingsteam basert på hastighet eller budsjett. Hvis koden din ender opp i noe som helst kritisk - som betalinger, onboarding eller handelsplattformer - må kunden bevise at programvaren er sikker, testet og sporbar fra ende til annen.
Så hvordan ser det egentlig ut i praksis? Innkjøpsteam ber nå om ting som sikker SDLC-dokumentasjon, automatiserte testlogger og rapporter om sårbarhetsskanning på forhånd. Kontraktene oppdateres med klausuler om robusthet som dekker alt fra gjenopprettingstider for sikkerhetskopier til ansvar for hendelsesrespons. Noen selskaper gjennomfører til og med felles testøkter med leverandørene sine for å stressteste responstidene. Poenget er at hvis du bygger finansiell programvare for en kunde, er du nå en del av deres compliance-historie.
Jeg håper du går fra dette innlegget med en følelse av å være litt tryggere på DORA - eller i det minste at du stiller deg selv de riktige spørsmålene. Og ærlig talt, det er allerede et stort skritt. Enten du så vidt har begynt å sette deg inn i regelverket eller er i full gang med å implementere det, trenger ikke veien til samsvar å være overveldende.
Vi i Innowise er her for å hjelpe deg med å finne frem i DORA-labyrinten, bygge ekte digital motstandskraft og beskytte virksomheten din, ikke bare nå, men også i fremtiden.

FinTech-ekspert
Siarhei leder FinTech-avdelingen vår med dyp bransjekunnskap og et klart syn på hvor digital finans er på vei. Han hjelper kundene med å navigere i komplekse regelverk og tekniske valg, og utformer løsninger som ikke bare er sikre - men som også er bygget for vekst.









Meldingen din er sendt.
Vi behandler forespørselen din og kontakter deg så snart som mulig.

Ved å registrere deg godtar du vår Retningslinjer for personvern, inkludert bruk av informasjonskapsler og overføring av dine personopplysninger.